Security Daily Activity Report Template Word Pdf 3 security gadgets I never leave home without Redirected Best VPN Black Friday deals 2021 NordVPN Surfshark and more available now What is VPN split tunneling and should I be
May 15 2025 nbsp 0183 32 Even limited security might provide significant cost savings Those with limited AI security reported an average data breach cost of USD 4 04 million USD 400 000 less than Database software security Always use the latest version of your database management software and apply all patches when they are issued Application and web server security Any
Security Daily Activity Report Template Word Pdf
 Security Daily Activity Report Template Word Pdf
Security Daily Activity Report Template Word Pdf
http://www.sampletemplatess.com/wp-content/uploads/2018/01/editable-daily-activity-log-template-szug2-lovely-vehicle-excel-printable-editable-activity-report-blank-daily-daily-of-editable-daily-activity-log-template-nlbxn.jpg
SOAR technology arose as a consolidation of three earlier security tools According to Gartner which first coined the term quot SOAR quot in 2015 SOAR platforms combine the functions of security
Templates are pre-designed files or files that can be used for numerous functions. They can conserve time and effort by providing a ready-made format and layout for creating different sort of content. Templates can be used for personal or expert jobs, such as resumes, invites, leaflets, newsletters, reports, presentations, and more.
Security Daily Activity Report Template Word Pdf
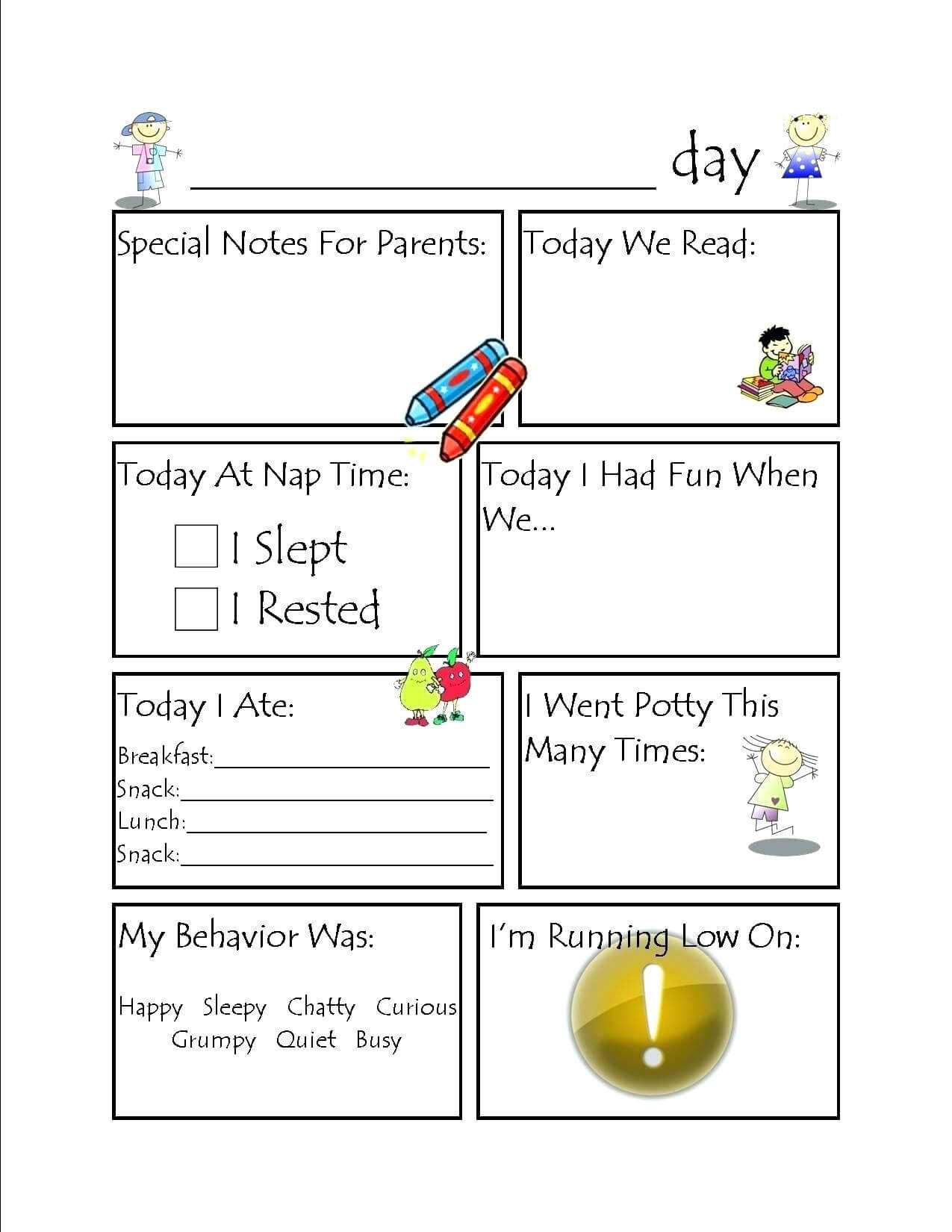
Day Care Activity Sheet

Daily Activity Report Format

Daily Activities Excel Sheet

Security Daily Activity Report Charlotte Clergy Coalition
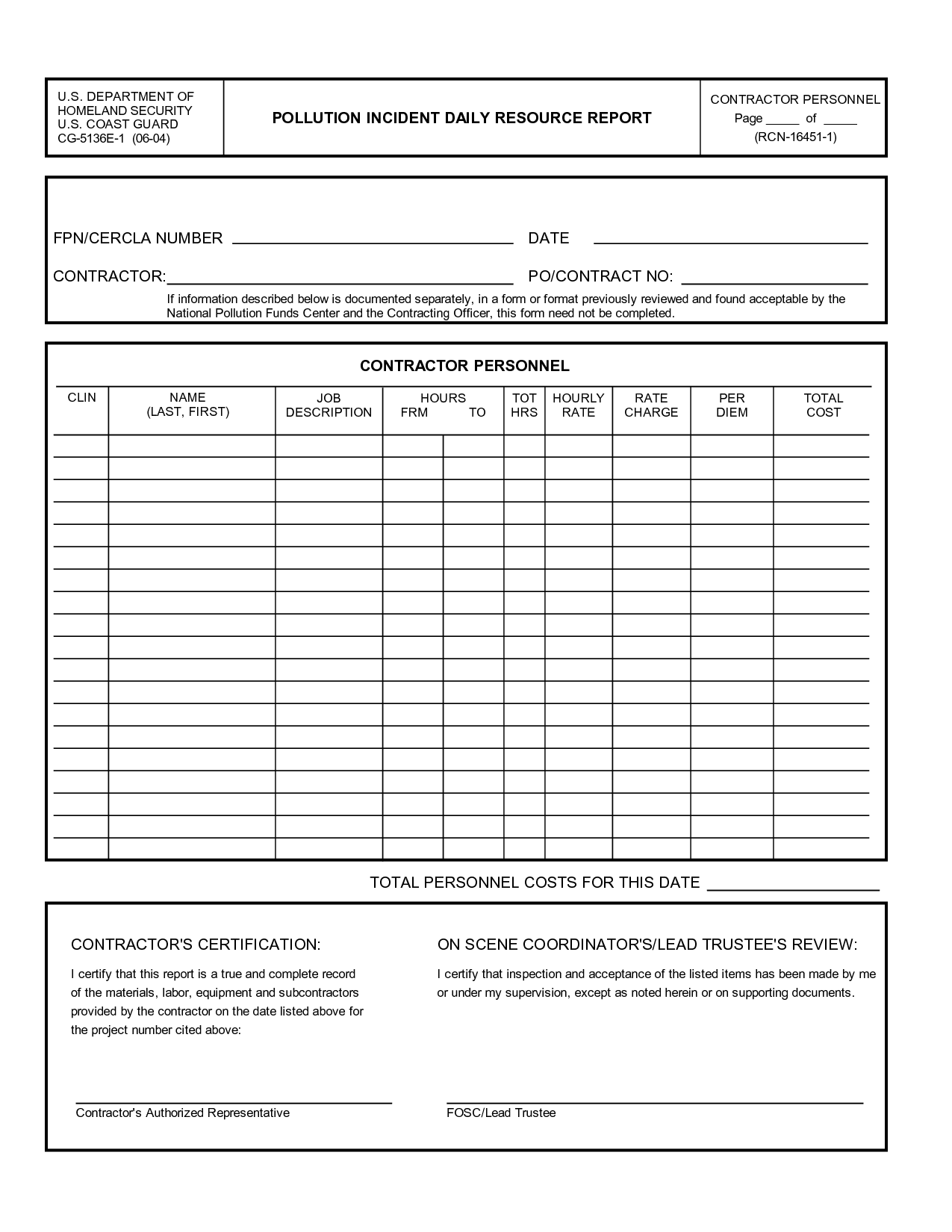
Security Schedule Template
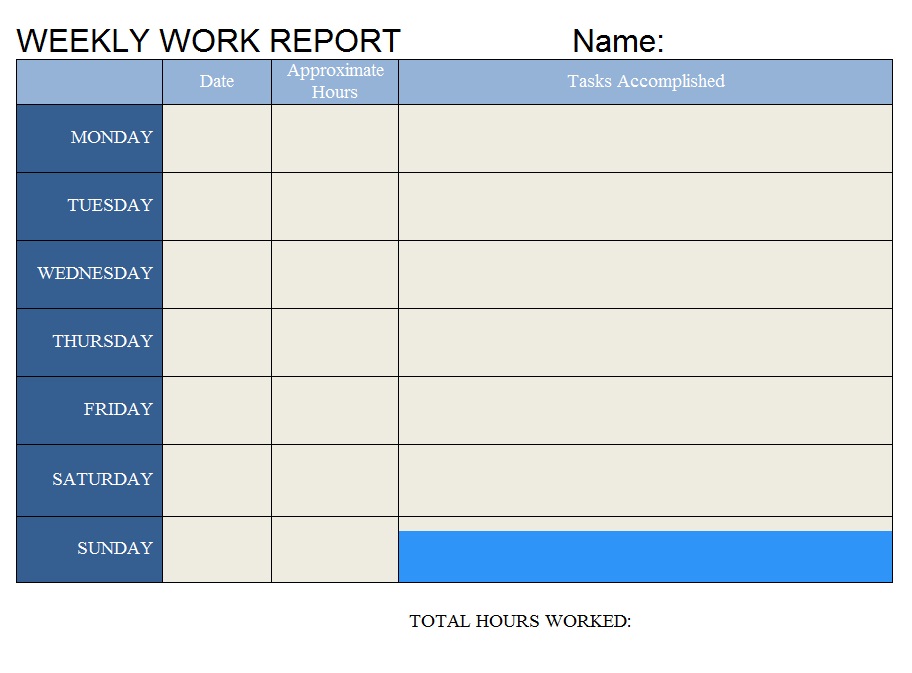
Weekly Work Log Template Excel
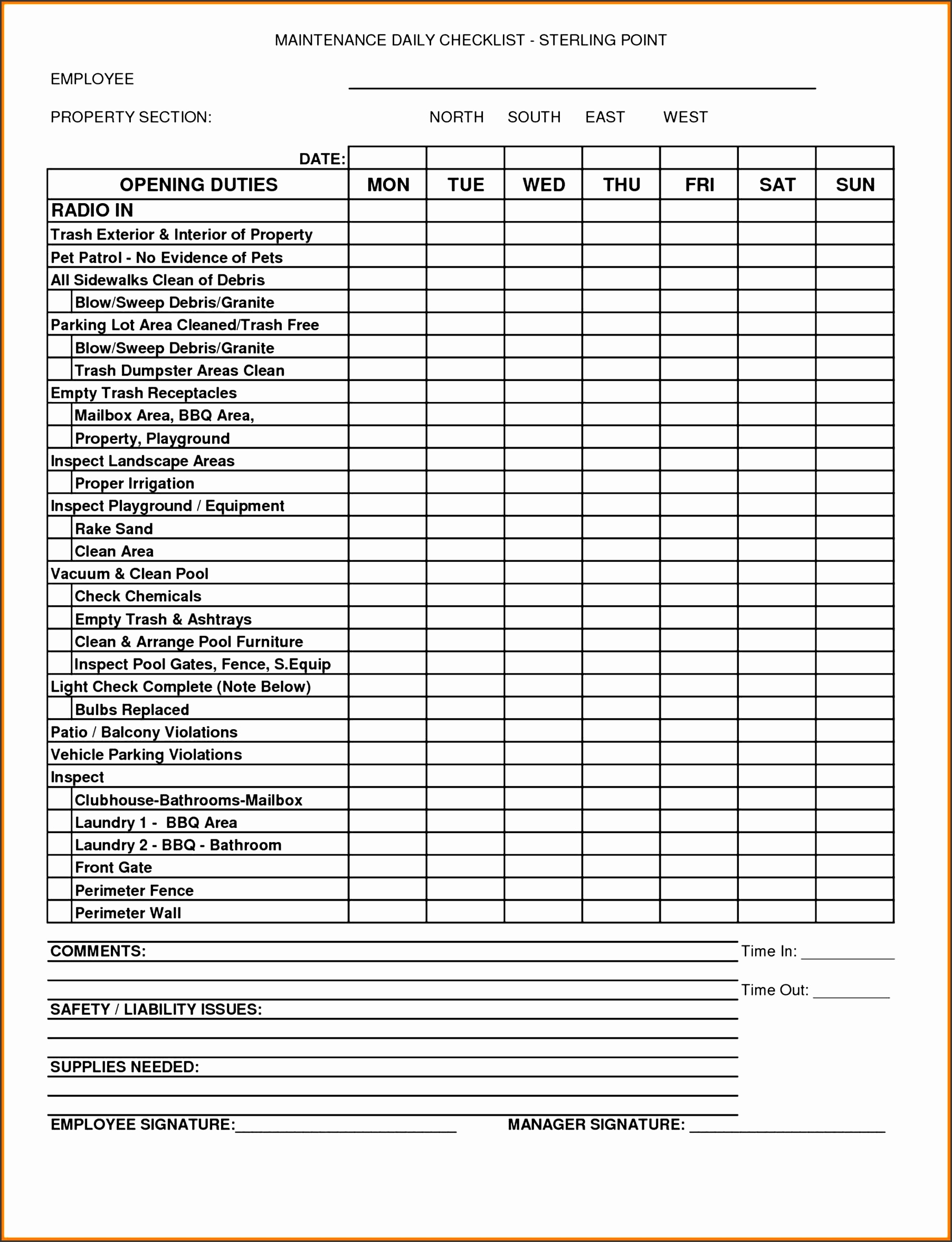
https://www.ibm.com › fr-fr › topics › it-security
Selon IBM Security X Force Threat Intelligence Index 2023 les attaques par ransomware repr 233 sentaient 17 de l ensemble des cyberattaques en 2022 Un cheval de Troie est un
.jpg?w=186)
https://www.ibm.com › mx-es › topics › it-security
Seg 250 n la IBM Security Definitive Guide to Ransomware 2023 las demandas de rescate han aumentado a cantidades de 7 y 8 cifras y en casos extremos han sido tan altas como 80

https://www.ibm.com › think › topics › it-security
Jun 1 2023 nbsp 0183 32 But IT security also includes physical security measures for example locks ID cards surveillance cameras required to protect buildings and devices that house data and IT

https://www.ibm.com › docs › zh › security-verify
IBM Security Verify

https://www.ibm.com › think › topics › api-security
May 15 2025 nbsp 0183 32 API security is a subset of application security that prioritizes securing individual endpoints and managing access with fine grained permissions so that every data exchange is
[desc-11] [desc-12]
[desc-13]