Security Guard Shift Hours May 15 2025 nbsp 0183 32 AI security means different things in different contexts While the focus of this page is the use of AI to improve cybersecurity two other common definitions center on securing AI models and programs from malicious use or unauthorized access In one definition cybersecurity experts focus on how threat actors are using AI to improve their cyberattacks or exploit new
Jul 26 2024 nbsp 0183 32 Information security InfoSec is the protection of important information against unauthorized access disclosure use alteration or disruption Jun 1 2023 nbsp 0183 32 What is IT security IT security which is short for information technology security is the practice of protecting an organization s IT assets computer systems networks digital devices data from unauthorized access data breaches
Security Guard Shift Hours
 Security Guard Shift Hours
Security Guard Shift Hours
https://i.pinimg.com/originals/57/a5/62/57a5624e73d14571be0a3b98c22e6324.jpg
Sep 30 2024 nbsp 0183 32 AI arguably poses a greater data privacy risk than earlier technological advancements but the right software solutions can address AI privacy concerns
Pre-crafted templates use a time-saving service for producing a diverse series of documents and files. These pre-designed formats and layouts can be made use of for different individual and professional jobs, consisting of resumes, invitations, flyers, newsletters, reports, discussions, and more, simplifying the content development process.
Security Guard Shift Hours

3 Crew 12 Hour Shift Rotation FREE 15 Sample Rotation Schedule

Rotating 12 Hour Shift Schedule Template Coverletterpedia

Jimmy Kimmel Live s Guillermo Rodriguez Got His TV Job After Being

AJK Azad Jammu Kashmir Power Development Organization Jobs 2020 Latest
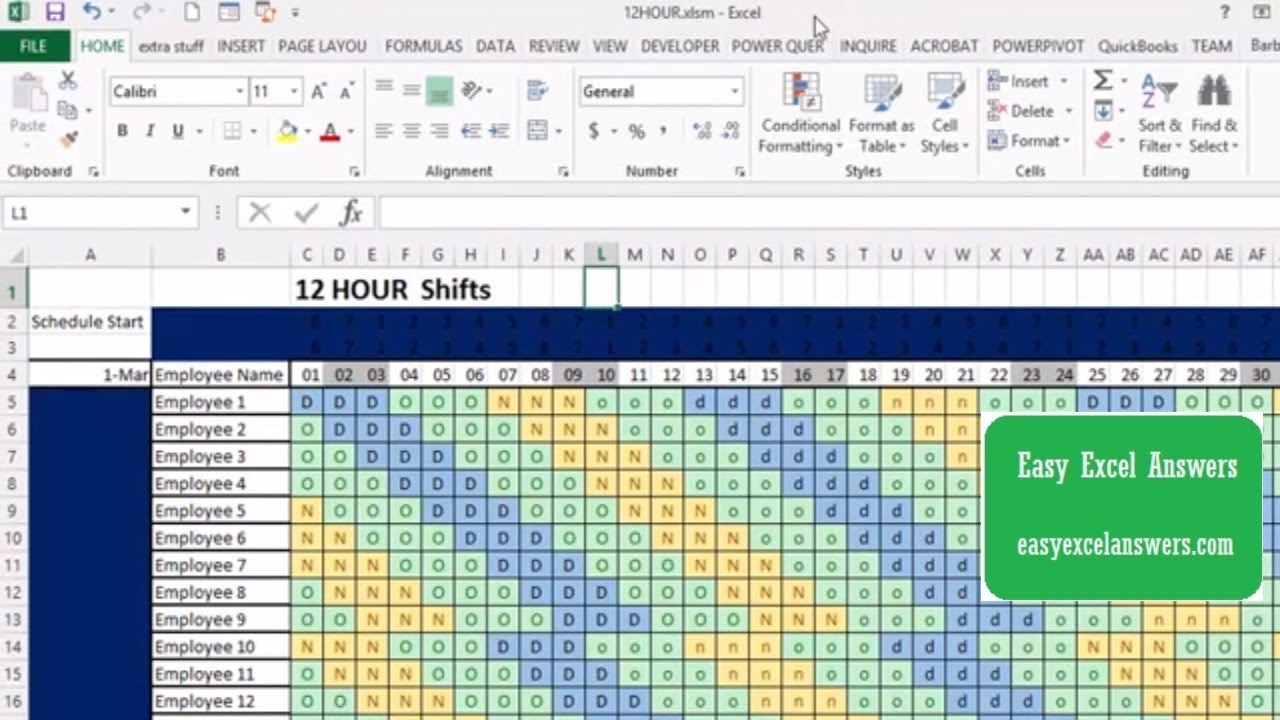
12 Hour Rotating Shift Schedule Calendar Example Calendar Printable

Security Guard Duty Roster Template Bdafinder

https://www.ibm.com › think › topics › cybersecurity
Jun 13 2025 nbsp 0183 32 Cybersecurity is the practice of protecting people systems and data from cyberattacks by using various technologies processes and policies At the enterprise level cybersecurity is key to overall risk management strategy and specifically cyber risk management Common cybersecurity threats include ransomware and other malware phishing scams data

https://www.ibm.com › think › topics › tokenization
Jan 27 2025 nbsp 0183 32 What is tokenization In data security tokenization is the process of converting sensitive data into a nonsensitive digital replacement called a token that maps back to the original Tokenization can help protect sensitive information For example sensitive data can be mapped to a token and placed in a digital vault for secure storage

https://www.ibm.com › reports › data-breach
IBM s global Cost of a Data Breach Report 2025 provides up to date insights into cybersecurity threats and their financial impacts on organizations

https://www.zdnet.com › topic › security
ZDNET news and advice keep professionals prepared to embrace innovation and ready to build a better future

https://www.zdnet.com › article
Jul 9 2025 nbsp 0183 32 Don t want to fork over 30 for a one year subscription to Windows 10 Extended Security Updates Microsoft is offering a couple of ways to avoid the fee But there is a catch
[desc-11] [desc-12]
[desc-13]